LDAP Integration -
Before we proceed for the lab setup I am using Microsoft Active Directory for LDAP. Its configured and setup - itlinks.com. Create 4-6 test users and one user with admin credentials - cpadminThere are multiple ways to authenticate or tie your users if you will to a centralized auth like LDAP. You can create users locally and give out id/password to your users, configure LDAP, RADIUS or TACACS ect to manage and give access to users. Once the LDAP is setup Check point then can make queries against the LDAP server and read the user data. The calls to the LDAP server can be encrypted (port 636) or unencrypted (port 389).
Create users locally - This is very simple method. If you have a small environment small number of users can be created manually with ease. But if you have 1000 users at that point you might consider integrating it with LDAP.
Backup the existing policy on which you have been working so far. Create a db revision to restore if any thing goes wrong.
Select the user container, right click select new user, select default.
In General properties enter the user name and other relevant information.

Option to create groups and club the users under groups is available as well. Since this is a local user creation under "Authentication" select "Check Point Password" and enter the password and save the user.
Example of group creation and adding the user to the group is below.
Create a user id (cpadmin) in AD to be used by checkpoint exclusively to query the LDAP db.
Create a bridge from checkpoint to LDAP server.
Create a LDAP group that utilizes this bridge and gets the user information.
I created a group called "Firewall" in the AD and in that group I have the users as listed below -
Next open the "Global properties" from Smart Dashboard and check the below option -
Again from the dashboard open "Launch Menu" --> Manage --> "Servers and OPSEC Applications"
It opens up a window, internal_ca is default value that is pre populated. To create bridge click "New" and select "LDAP Account Unit"
Here in the LDAP account unit the AD server details and id that has rights to query the AD needs to be entered as shown below. If you also want to manage CRL and users check the boxes highlighted below.
Servers tab is used to add the LDAP server itself and provide the user details. Click "Add"
I created an object called "MainDC" which is the active directory server. Port is selected as 389 and input the other info as per the screen print. Check the encryption when you can setup the secure communication. I would advice if its a production to go and use that option,but here since this is a lab setup I will use the unsecured communication.
Click ok and you will see -
Select the "Object Management" tab and click on "Fetch Branches" tab, if the config is correct it will query the AD and display as below
Finally on the "Authentication" tab select "Checkpoint Password"
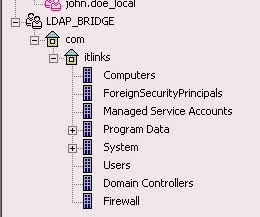
Once the bridge config is done, its visible under "Users and Administration" container. Right click and choose "Update tree" , its going to pull the entire AD content..
So this is how we link check point to LDAP server.
















No comments:
Post a Comment